Supplier Risk Management Guide
According to §17 NIS-Law (BGBL I Nr. 111/2018) and replaced by §32 NISG 2026 (BGBL I Nr. 94/2025) on 1.10.2026, operators of essential services must also ensure that their suppliers take appropriate technical and organizational security precautions. This is also relevant for all companies in the financial services sector, as the regulation on digital operational resilience in the financial sector (DORA), which applies to them since 17 January 2025, also requires strict management of third-party service providers.
The Austrian NIS authority (Federal Office for Cybersecurity) expects several thousand companies to be affected from the sectors (excerpt):
- Energy
- Banking & Financial Market Infrastructures
- Healthcare
- Digital infrastructure
- IT Services & Management
- Public administration
- Road and rail transport
- Postal and courier services
- Aerospace
- Water Management
- Waste management
- Manufacturing, production and distribution of chemicals
- Production, processing and distribution of food
- Manufacturing (medical equipment, computers, electronic and optical products, electrical equipment, machinery, automobiles, trailers and other transportation equipment)
- Digital providers (marketplaces, search engines, social networking platforms)
- Research Organization
This regulation extends far into the SME sector and affects many companies that have not yet implemented structured supplier risk management. To support these businesses, Cyber Trust Services has partnered with the KSV1870 to put together a comprehensive package for operators of essential and important services to make it as easy as possible for them to get started with supplier (risk) management.
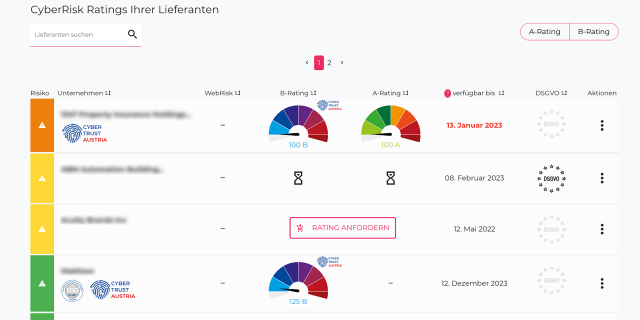
The KSV1870 provides an integrated supplier risk management platform (CyberRisk Manager). Your benefits:
- Upload of all suppliers to the platform
- Creation of a web risk rating for all uploaded suppliers
- Display which of the suppliers already have a Cyber Trust Quality Seal
- Display which of the suppliers have ISO 27001 certification
- Option for suppliers without a seal of approval or certification to request a (paid) KSV1870 Cyber Risk Rating
- Use of the platform for any number of users in the company (e.g. procurement department, security department, etc.)
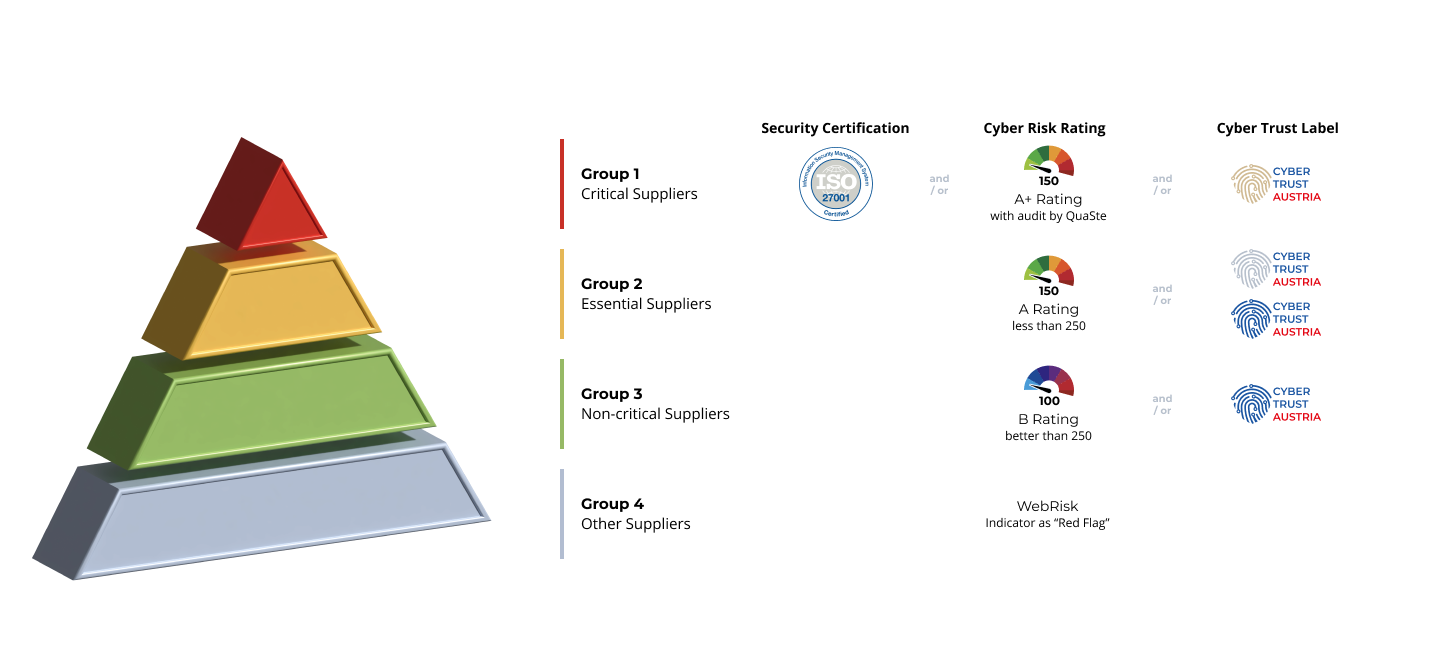
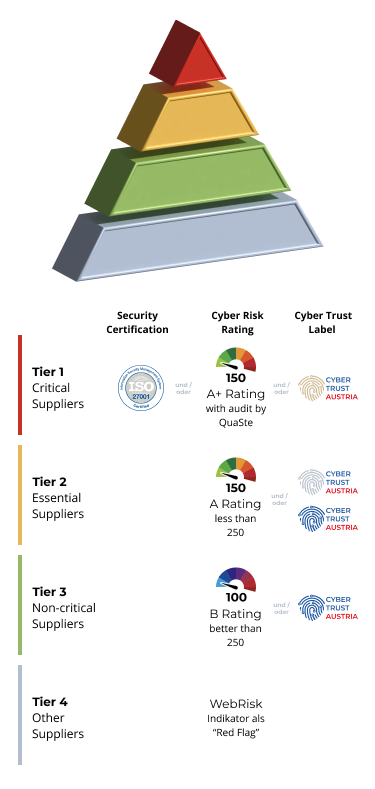
Suplier Risk Management Process
In addition to the technical implementation of supplier management, it is also essential to set up an efficient supplier risk management process, because not every supplier is equally critical and not every supplier requires the same cybersecurity requirements.
In collaboration with the University of Applied Sciences Upper Austria, we have developed a ground-breaking method and an innovative tool for categorizing and classifying supply chain partners in the area of cybersecurity. We are happy to make this available to you for free use in your own company ("as is"). At the moment the tool is available for Office 365. Terms of use see disclaimer in the tool.